You are viewing the RapidMiner Server documentation for version 9.7 - Check here for latest version
Configuring Radoop Proxy Security
RapidMiner Radoop makes it possible to connect to the Hadoop cluster via the Radoop Proxy service, which can be installed along with RapidMiner Server. This guide explains how to establish secured connections between:
- RapidMiner Studio and Radoop Proxy
- Radoop Proxy and RapidMiner Server.
Creating a secure Radoop Proxy Connection
If you aim to establish an SSL-encrypted Radoop Proxy connection, please take the following steps:
-
Find and open the proxy configuration file, which is located at
radoop-proxy/proxy.propertiesin the RapidMiner Server installation directory by default. -
To enable SSL connections,
sslEnabled=trueproperty setting is required. Furthermore, you have to define the private key by uncommenting (remove#character) and setting the following lines, like:keystorePath=<keystore_file>keystorePassword=<private_keypass>
-
Create a new Radoop Proxy Connection from RapidMiner Studio or from RapidMiner Server (for the latter option, make sure that Radoop extension is installed on RapidMiner Server).
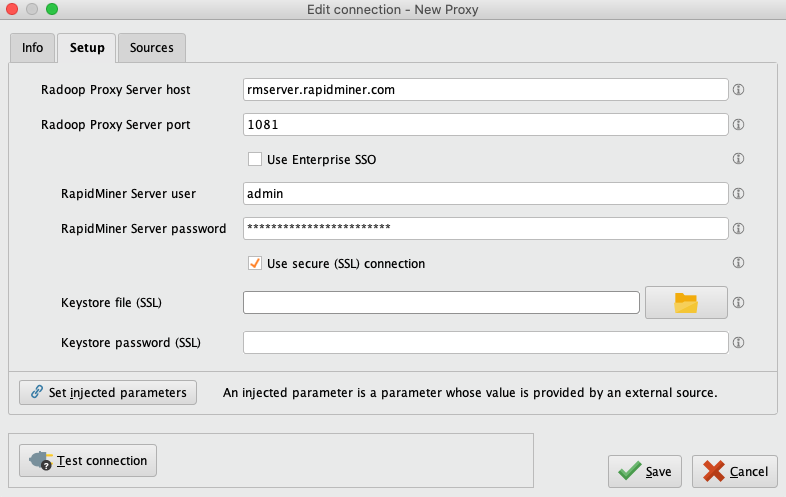
Provide the location of Radoop Proxy server and RapidMiner Server credentials, and check Use SSL and leave the Keystore file and Keystore password fields empty.
Click ![]() Test connection to check whether the Radoop Proxy connection was configured correctly.
Test connection to check whether the Radoop Proxy connection was configured correctly.
-
Generate the keystores. Run the following commands (for further customization parameters, see Oracle documentation).
keytool -genkeypair -alias server -keyalg RSA -keypass <private_keypass> -storepass <private_keypass> -keystore server-keystore.jks keytool -exportcert -alias server -storepass <private_keypass> -file server.cer -keystore server-keystore.jks keytool -importcert -v -trustcacerts -alias server -file server.cer -keystore client-trust-keystore.jks -keypass <public_keypass> -storepass <public_keypass> rm server.cerNote down all passwords, as they will be needed in the following steps.
-
Find and open the proxy configuration file, which is located at
radoop-proxy/proxy.propertiesin the RapidMiner Server installation directory by default. -
To enable SSL connections,
sslEnabled=trueproperty setting is required. Furthermore, you have to define the generated private key of Radoop Proxy by uncommenting (remove#character) and setting the following lines, like:keystorePath=keystore.jkskeystorePassword=<private_keypass>
Use the same password (
<private_keypass>) that you provided in Step 1. -
Create a new Radoop Proxy Connection from RapidMiner Studio or from RapidMiner Server (for the latter option, make sure that Radoop extension is installed on RapidMiner Server).
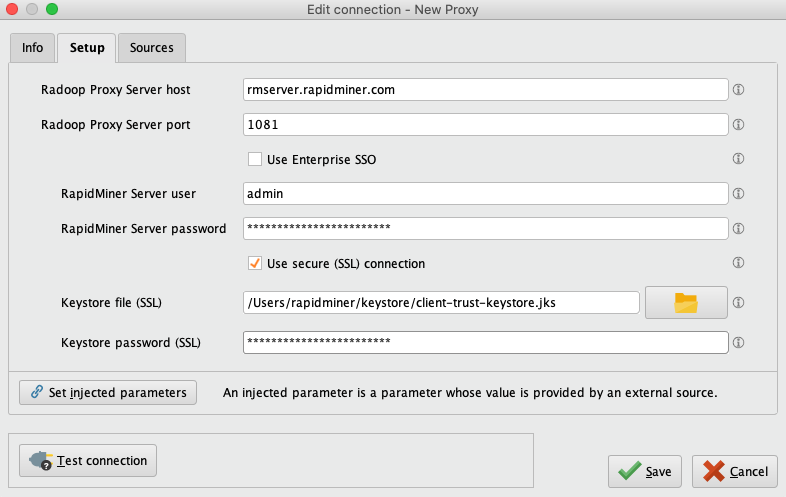
Provide the location of Radoop Proxy server and RapidMiner Server credentials. Check Use SSL, and fill in the required fields:
- Keystore file: Insert the private keystore file (
client-trust-keystore.jks) location here. - Keystore password: Type in the
<public_keypass>used in Step 1.
Click ![]() Test connection to check whether the Radoop Proxy connection was configured correctly.
Test connection to check whether the Radoop Proxy connection was configured correctly.
Establishing HTTPS connection between Radoop Proxy and RapidMiner Server
If HTTPS connection is configured for RapidMiner Server with a well-known certificate, you can make Radoop Proxy use the HTTPS port for authentication. To make these changes, open the proxy configuration file (radoop-proxy/proxy.properties in the RapidMiner Server installation directory) and find the two blocks after # authentication by RapidMiner server line. Comment out the first block, and uncomment the second one (add and remove # signs, respectively):
# authentication by RapidMiner server
#serverAuthenticationScheme=http
#serverAuthenticationHost=localhost
#serverAuthenticationPort=8080
#serverAuthenticationUrl=/api/rest/instance
serverAuthenticationScheme=https
serverAuthenticationHost=localhost
serverAuthenticationPort=8443
serverAuthenticationUrl=/api/rest/instance
Make sure that the property values match your RapidMiner Server configuration.