You are viewing the RapidMiner Radoop documentation for version 2024.0 - Check here for latest version
Installing Radoop on Altair AI Hub
This documentation assumes that Altair AI Hub is deployed using a containerized deployment method, and that a working Radoop connection is available in a repository or project, as described in Configuring Radoop connections. In others cases please consult the previous version of this documentation.
Prerequisites
The following requirements must be met before using Radoop in Altair AI Hub:
- Radoop Extension installed and tested in Altair AI Studio.
- A working Radoop connection to a Hadoop cluster in Altair AI Studio, stored in a repository or project. See Configuring Radoop Connections to learn how to create it.
- The same version of the Radoop extension installed in Altair AI Hub. (Containerized deployments ship with a bundled Radoop extension, so you only need to ensure the version match.)
- A valid license for Radoop installed in Altair AI Hub. You can obtain your license from your RapidMiner Account portal.
Installing Radoop on Altair AI Hub and the connected Job Agent(s)
As the Radoop extension is already in place on Altair AI Hub when using our containerized deployment, the only needed step is to install your Radoop license obtained above.
To do this, log in to Altair AI Hub as an administrator, then click on the Install license action on the Administration --> Manage licenses page and paste your Radoop license key.
Using Radoop connections with Altair AI Hub
Using Radoop connections with Altair AI Hub is as easy as it is with Altair AI Studio, but there are some caveats which will be discussed in detail below. The Radoop connection used by the process being executed in Altair AI Hub must be in the same repository or project.
Important note: Radoop processes are not supported in Altair AI Hub web services.
Managing multiple Hadoop users with Altair AI Hub executions
When multiple users are running Radoop processes in Altair AI Hub, it's a natural expectation that the jobs created on the Hadoop cluster by Radoop all run as individual users, for auditability.
It is also expected that such clusters are secured using Kerberos and keytabs are used for authentication, each user having their own keytab.
By using Altair AI Hub's vault to securely store these keytabs for each user, it is possible to create a connection that uses each user's own keytab directly from the vault.
To do this, the connection manager or administrator setting up the connection for other users must edit the exported Radoop connection, then click Set injected parameters on the Security tab and select the Kerberos keytab parameter to be injected from Altair AI Hub.
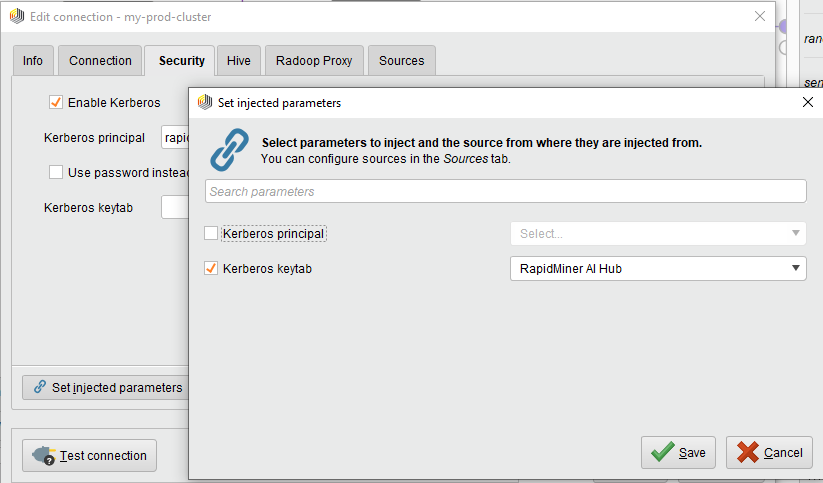
Note: the Altair AI Hub injection option is only available when the Radoop connection is stored in an Altair AI Hub project. The legacy repository is not supported.
Note: administrators must ensure that each user has a valid keytab injected into their user’s vault in Altair AI Hub. This task can be done using Altair AI Hub’s REST APIs, and it is much easier when automated using a script. Please contact our support team to provide a sample script if needed.
Using Radoop Proxy with Altair AI Hub executions
Using Radoop Proxy is mandatory for Altair AI Hub. It is enabled by default in connection creation time. If you would like to adapt an existing connection that did not have the Proxy enabled for Altair AI Hub, you can do so by completing the following steps:
Open the Manage Radoop Connections window and edit the original Radoop connection that was exported to a repository or project.
On the Altair AI Hub tab, check Force Radoop Proxy on AI Hub.
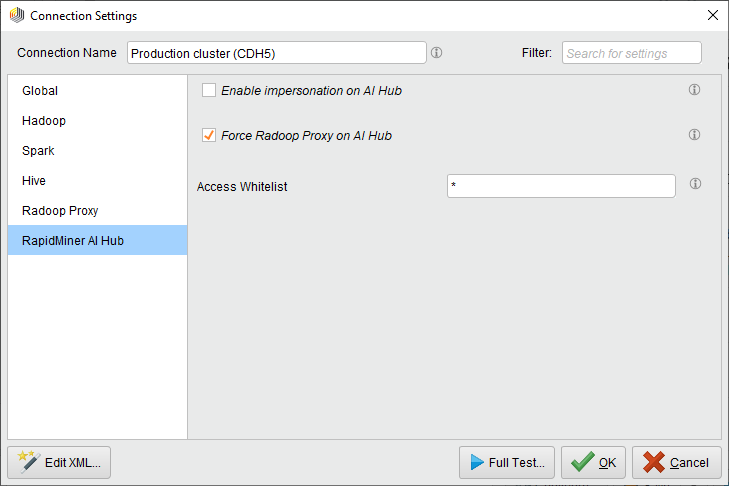
Save, then Export the connection to a repository or project.
Note: the Radoop connection and the Radoop Proxy connection must be in the same repository or project, and both need to be located on the same AI Hub where the execution will take place.