You are viewing the RapidMiner Legacy documentation for version 9.8 - Check here for latest version
Enabling HTTPS
To create secure connections between RapidMiner Studio and RapidMiner Server or for the Web UI, take the following steps:
Configure RapidMiner Server for HTTPS.
Reconfigure the connection between RapidMiner Server and the Job Agent
Reconfigure the connection between RapidMiner Server and RapidMiner Studio.
If you want to change the default port (8443) for HTTPS communication on the server side, see the section on changing ports.
Configure RapidMiner Server for HTTPS
Follow these steps to enable an SSL-encrypted connection:
Obtain an SSL certificate from a certificate authority of your choice. In order to configure HTTPS communication, you need to have a private key, a server certificate and an optional certificate chain of the issuer. Certificate issuers provide these data in various formats, which can be converted easily to the other formats:
- If using the PEM format, the private key is provided in a separated file with
.keyextension, while the certificate and the certificate chain in one or more files with.ceror.crtextension. These files are text based with BASE64 encoding. - The DER format provides the same structure: a separated private key file and certificate file(s), which are binary files with DER encoding.
- The PKCS#12 format is a bundle (keystore) in one file with
.p12or.pfxextension, that contains one or more set of "certificate related data" (private key, certificate and optional certificate chain) tagged with analias. Thealiasidentifies exactly the private key and certificate in the store file. - The JKS (Java Keystore) format is similar to the PKCS#12 format and used mainly in Java-based environments
Note: SSL certificates are issued per domain, per host name or for a set of subdomains (wildcard certificate). Make sure that the hostname of the certificate matches the hostname of your RapidMiner Server installation. Otherwise, accessing browsers will show warnings and may even block access entirely.
- If using the PEM format, the private key is provided in a separated file with
To install the certificate to RapidMiner server a JKS format is needed. Please consult the CA's documentation for instructions on converting it, check online available resources or check our examples here. OpenSSL is a freely available tool for managing and converting certificates, while keytool is included in Java installations for managing Java keystores (JKS).
Convert PEM certificate and private key to PKCS#12 format. Provide the certificate-related files, set an alias (e.g. "pkcs12alias") in the command line and the tool will ask for a password (Export password), that will be used to encrypt the PKCS#12 file.
openssl pkcs12 -export -out certificate.pfx -inkey privateKey.key -in certificate.crt -certfile chain.crt -name "pkcs12alias"The generated certificate bundle can be checked using the following command:
openssl pkcs12 -info -in certificate.pfxConvert PKCS#12 into JKS, using the Java keytool, as follows. Please check the filename parameters in the command line and take care on the alias names also. The
srcaliasshould be the same that was used previously during the export to the PKCS#12 format (name parameter). First the tool will ask for a password to decode the previously created PKCS#12 file (source keystore). Afterwards the tool will ask for a new password for the new JKS file (destination keystore password) and also the private key.keytool -importkeystore -destkeystore certificate.keystore -srckeystore certificate.pfx -srcstoretype PKCS12 -srcalias pkcs12alias -destalias jksalias -trustcacerts
Important limitation: In the JBoss configuration only one password can be provided, that will be used as the keystore password and also as the private key password, so these two passwords should be the same in the JKS file.
Copy the generated
certificate.keystoreto the folderconfiguration/in your RapidMiner Server home directory.Open the file
standalone.xml. It is located inconfiguration/of the RapidMiner Server home directory.Locate the tag
<connector name="https" ... />. Uncomment the following snippet directly below the tag (by deleting<!--and-->) and edit the password to match the password of your keystore and edit the alias field to match the alias name used during the JKS export. (If you cannot find the commented snippet, just copy the code below and paste it directly after the<connector name="http" ... />tag.). Please take care on the path of the keystore. If it is not located in the folder/rapidminer-server-home/configuration, then you can provide the full path also.<!-- <connector name="https" scheme="https" protocol="HTTP/1.1" socket-binding="https" enable-lookups="false" secure="true"> <ssl name="ssl" password="secret" protocol="TLSv1" key-alias="jksalias" certificate-key-file=" ${jboss.server.config.dir}/certificate.keystore" /> </connector> -->If ciphers need to be hardened, add the following attributes
cipher-suite="TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384,TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384,TLS_RSA_WITH_AES_256_CBC_SHA256" protocol="TLSv1.1,TLSv1.2"
to the element starting with<ssl name="ssl".., yielding:<ssl name="ssl" password="secret" protocol="TLSv1" key-alias="jksalias" certificate-key-file=" ${jboss.server.config.dir}/certificate.keystore" cipher-suite="TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384,TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384,TLS_RSA_WITH_AES_256_CBC_SHA256" protocol="TLSv1.1,TLSv1.2" />In case you are working with the up to date Oracle java, you may need to install Java Cryptography Extension (JCE)If you want to disable HTTP connections entirely and forward them to HTTPS automatically:
Add the flag
redirect-port="8443"inside the HTTP (not HTTPS) tag —<connector name="http" ... />. (Replace the port with your actual SSL port if it differs from the default):<connector name="http" ... redirect-port="8443" />Modify the
web.xmlfile, which can be found at/standalone/deployments/rapidminer-server-xxx.ear/rapidminer-server-war.war/WEB-INF/web.xmlof your RapidMiner Server installation directory, by adding the following:<security-constraint> <web-resource-collection> <web-resource-name>Secure Apps</web-resource-name> <url-pattern>/*</url-pattern> </web-resource-collection> <user-data-constraint><transport-guarantee>CONFIDENTIAL</transport-guarantee></user-data-constraint> </security-constraint>
Restart RapidMiner Server.
Reconfigure the connection in the Job Agent(s)
After configuring RapidMiner Server, you must also reconfigure each Job Agent that connects to this server. Follow these steps:
Locate the Job Agent's configuration file
agent.properties(located in thehome/configdirectory of the Job Agent deployment)Modify the
rapidminer.server.protocolproperty tohttpsModify the
rapidminer.server.hostandrapidminer.server.portproperties to contain the valid hostname and port configured for your server.
Reconfigure the connection in RapidMiner Studio
After configuring RapidMiner Server, you must also reconfigure each RapidMiner Studio instance that connects to this server. Follow these steps:
In RapidMiner Studio, right-click on the RapidMiner Server repository and select Configure Repository:
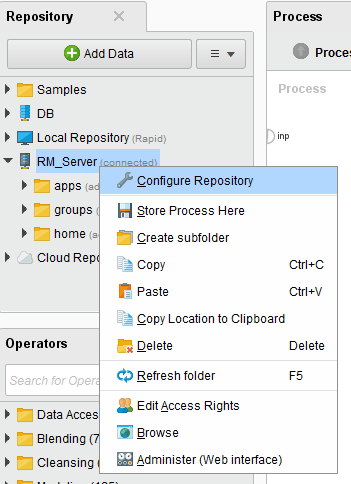
The Configure RapidMiner Server Repository window opens. Modify the Repository URL field to use SSL and match the port value you set for RapidMiner Server.
For example:
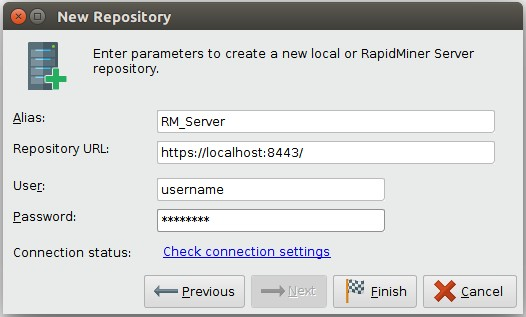
Click
 Save to save your changes.
Save to save your changes.